Users and Roles
Users can be created and assigned roles and/or claims to allow them to perform certain types of operations.
To create a new User
- Navigate to Users in the configuration’s Main Menu. Here you can add, edit, and view users. To add a user, click the New User button.
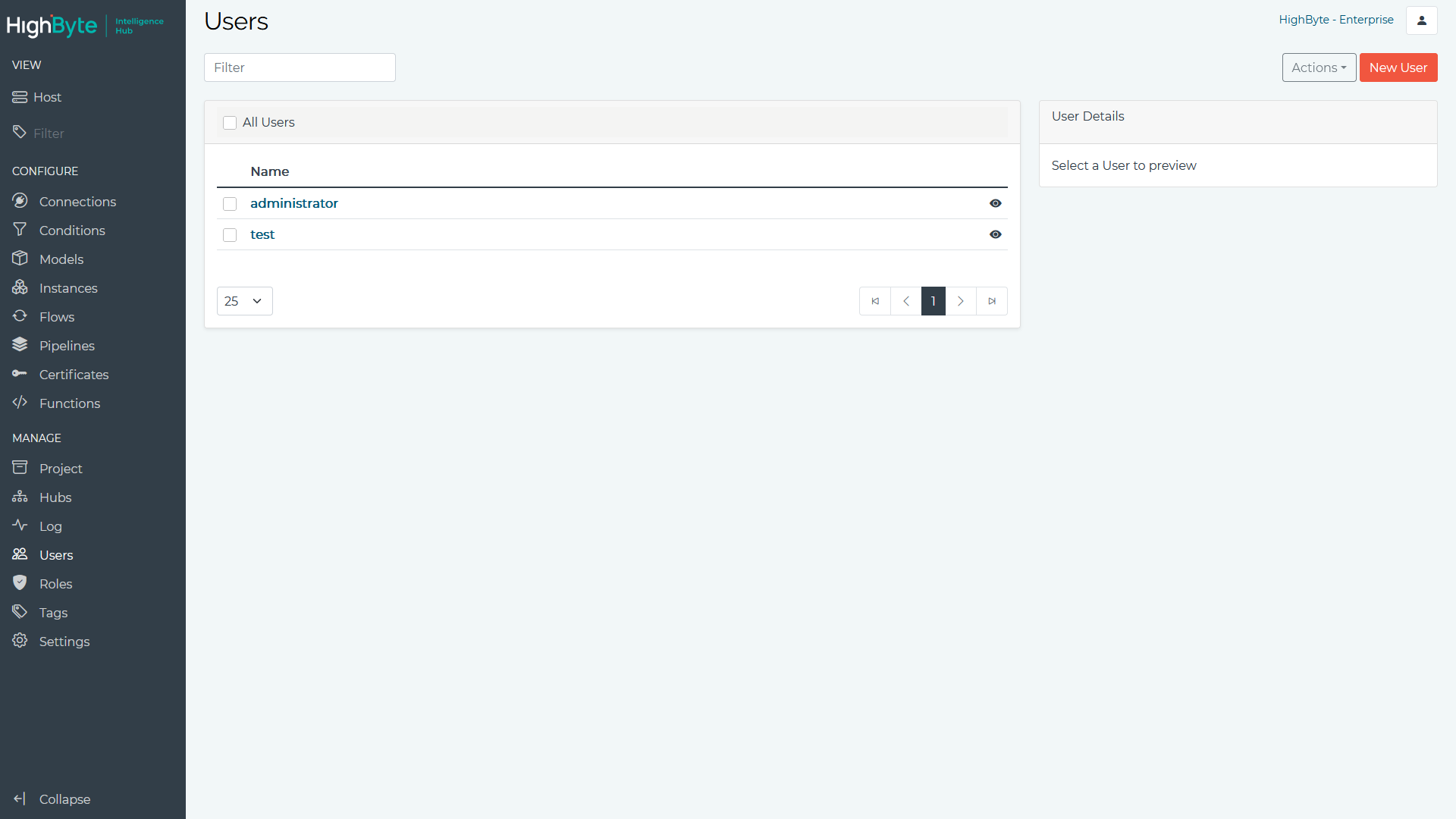
- Enter the Username and Password. Click Next to continue.
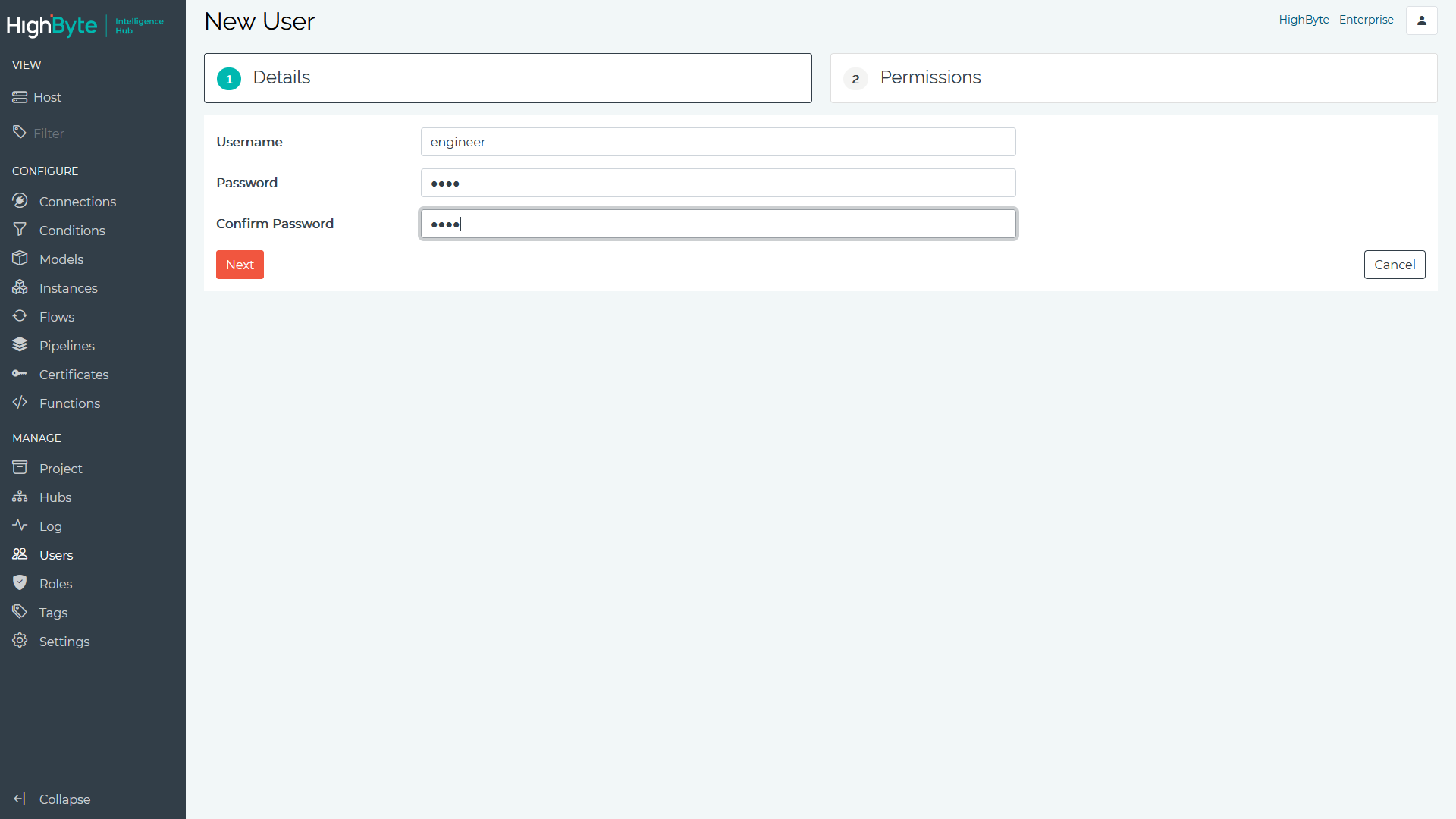
- Select the Roles and/or set the Claims the user inherits. Click Submit to add the user. Claims are specified through the usage of resources and actions. Resources are the object (e.g., connection) and actions are the operation that can be performed in CRUD terminology (create, read, update, delete) on a resource.
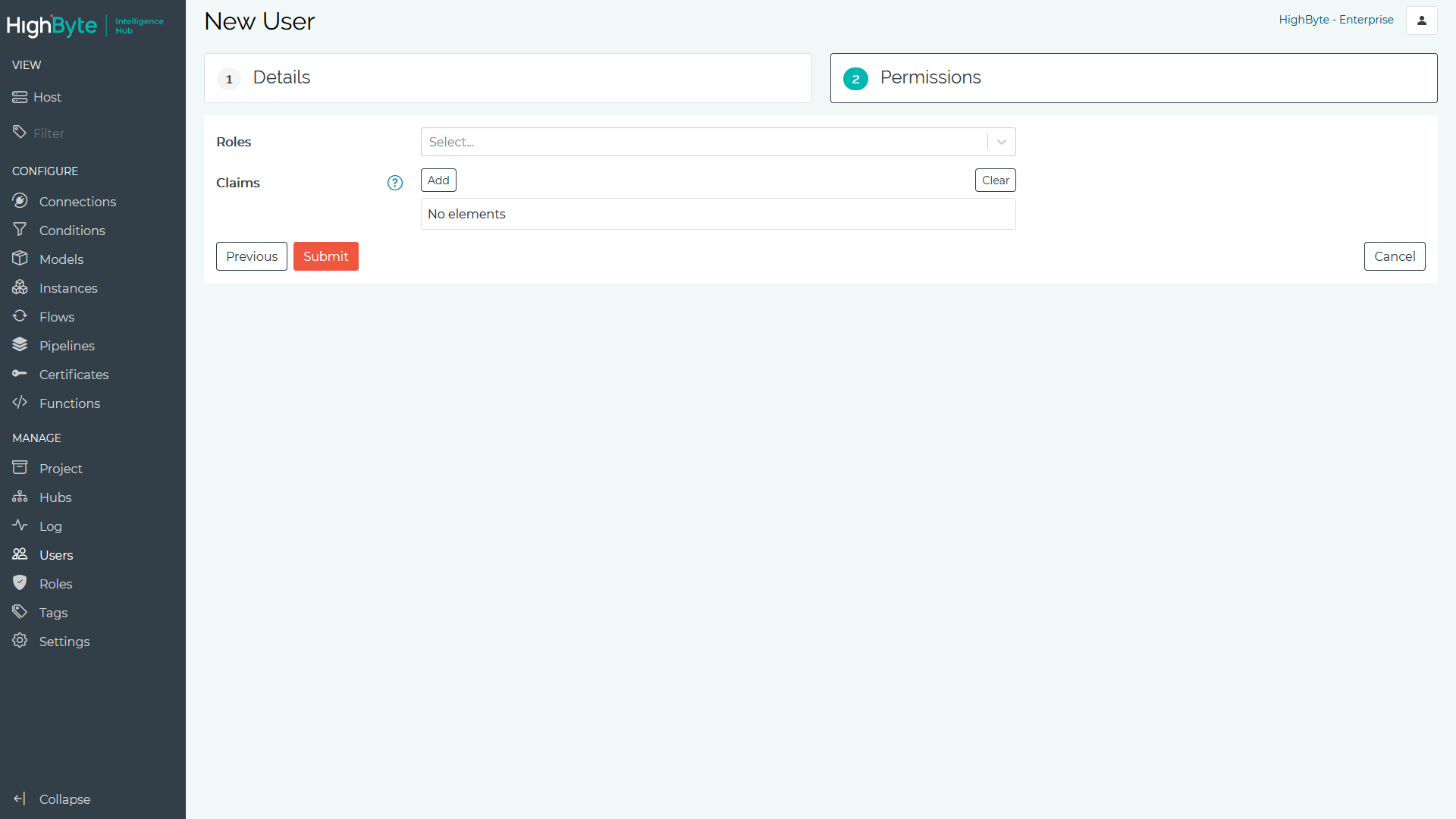
To create a new Role
Roles can be created and assigned claims that are inherited by one or more users. The roles define the type of operations a class of users may perform.
- Navigate to Roles in the configuration’s Main Menu. Here you can add, edit, and view roles. To add a role, click the New Role button.
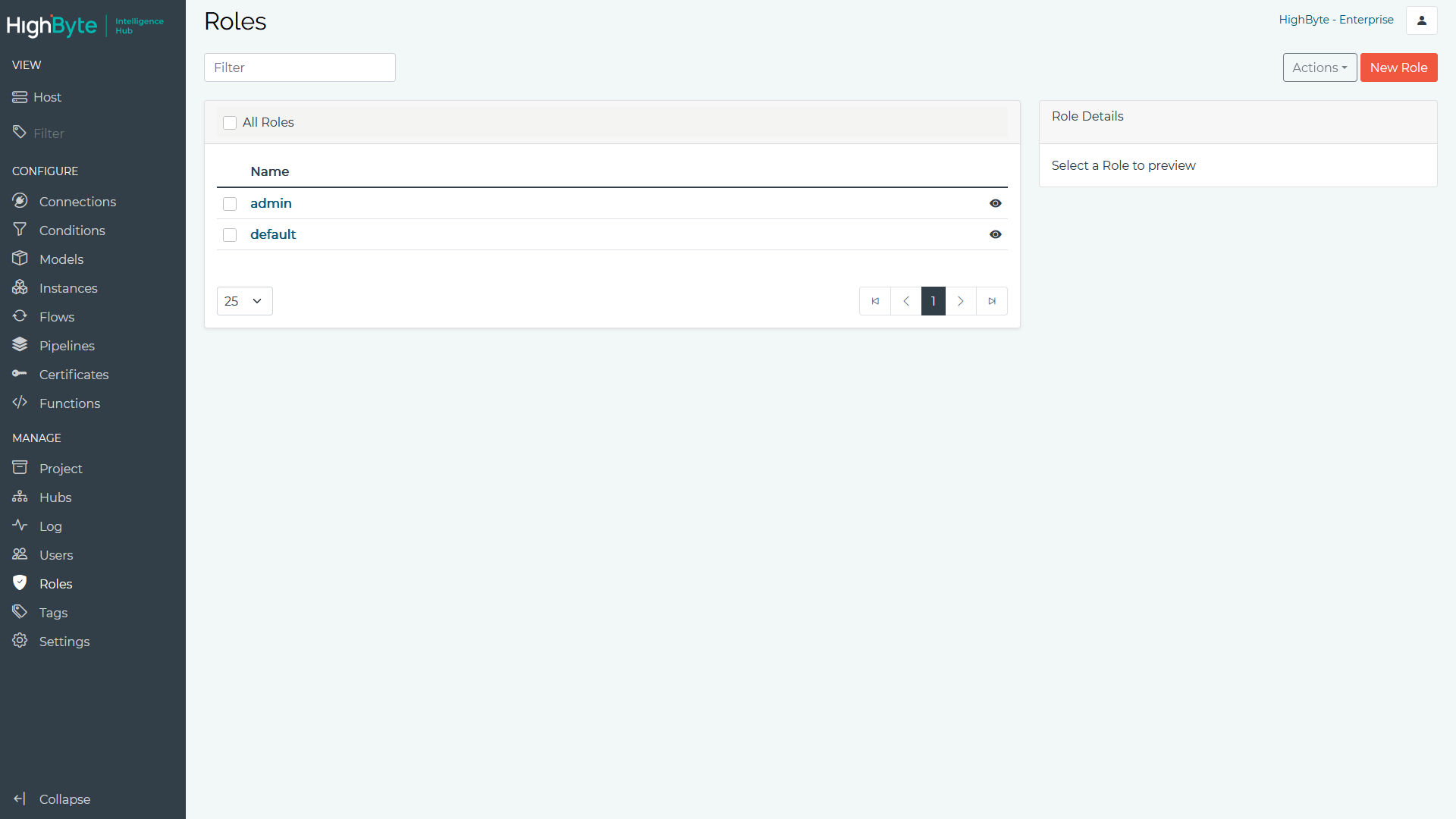
- Enter a Name to represent the new role.
- Set the Claims the user assigned to this role should inherit. Click Submit to add the role.
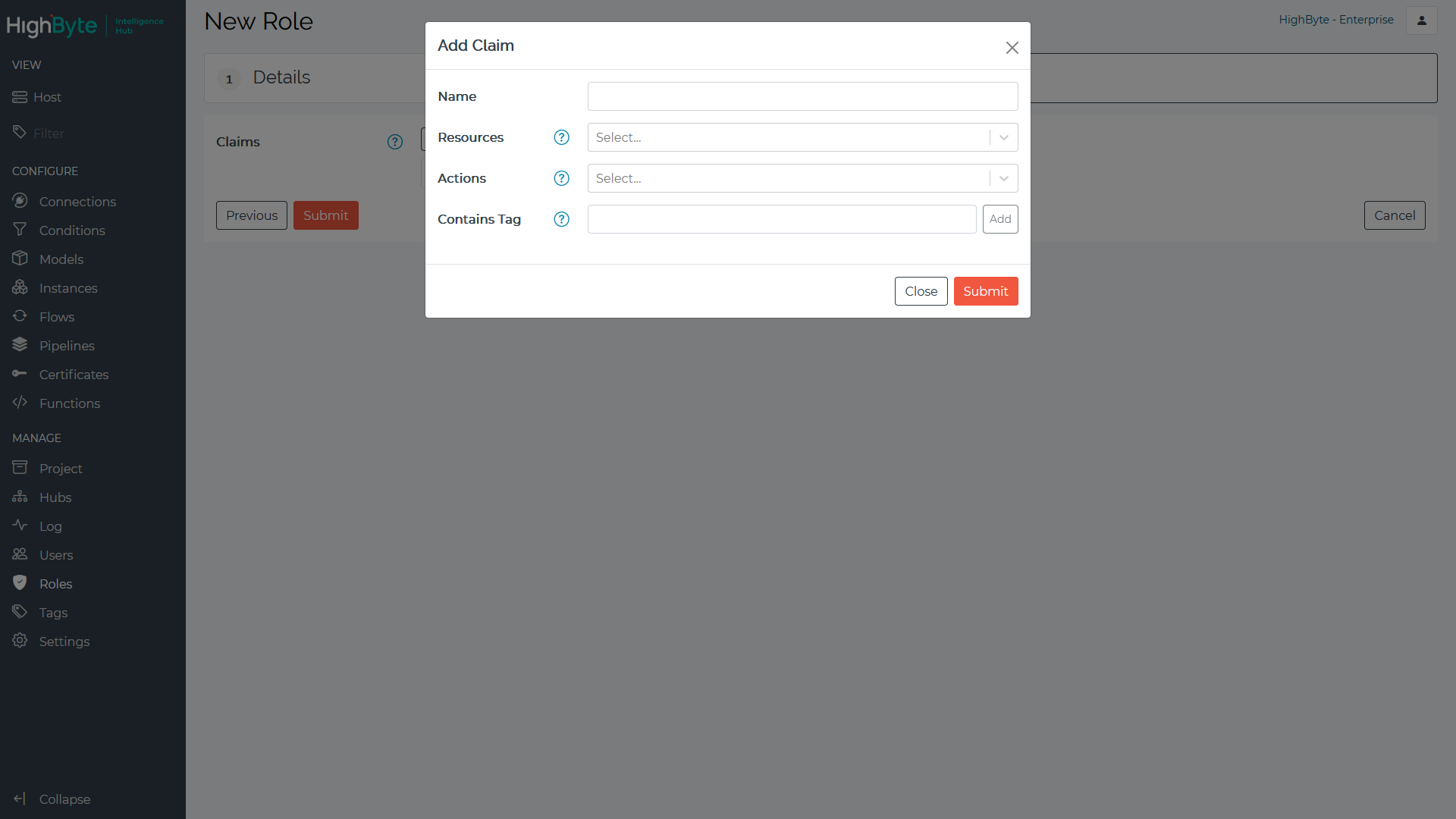
Claim Information
Supported Resources
| Resource | Description |
|---|---|
| * | Specifies all resources |
| broker | MQTT Broker |
| certificate | Certificates |
| connection | Connections, includes inputs and outputs |
| condition | Conditions |
| flow | Flows |
| function | Global functions |
| instance | Instances |
| log | The event log |
| model | Models |
| pipeline | Pipelines |
| network | Network hubs, groups, and sync operations |
| Settings | System level settings |
| tag | Tags |
| user | Users and roles |
Supported Actions
| Action | Description |
|---|---|
| * | Specifies all actions |
| create | Create new resource |
| read | Read resource |
| list | Retrieve a list of resources |
| update | Edit resource |
| delete | Delete resource |
| execute read | Read data for a source (ex. Input or Instance) |
| execute write | Write data to a target (ex. Output or Pipeline) |
| publish | Publish to an MQTT broker topic |
| subscribe | Subscribe to an MQTT broker topic |
Supported Scopes
| Scope | Description |
|---|---|
| Contains Tag | Limits access to resources tagged by one of the specified tags (this scope only applies to Connections, Conditions, Models, Instances, and Flows) |
API Keys
API Keys can be created and assigned to a user to limit access to the REST Data Server.
User API keys have a name, expiration date (optional) and description. Once created, the API key can be used as part of the REST Data Server login. See Application Settings for details on token based login.
As an example, to limit write access to an OPC UA connection through the REST Data Server, create a claim for the user with the execute write action on a connection resource,
tag the connection with a new tag (ex. opcua_write), and include the tag in claim.